- HOME
- ESG
- Information Security

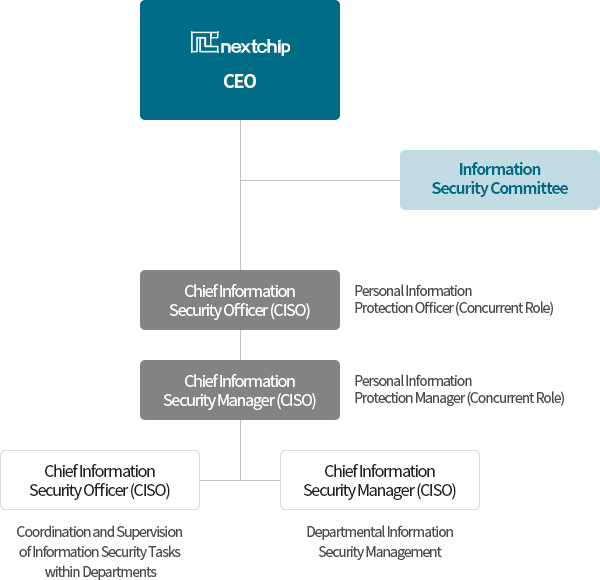
Information Security
Establishing the companywide security regulations and guidelines that integrate information security/asset management, personnel security, physical security, and information technology security, etc.
Assigning the duty of protecting our information through compliance with personal information laws and establishment of personal information processing methods, etc.
01.Acquired ISO 27001 certification to strengthen the corporate responsibility for information protection
02.Protecting the corporate asset safely based on the companywide security regulations and guidelines, and operating 13 basic policies including the Information Security Policy to respond to security accidents, efficiently
- Information Assets
- Asset Classification
- Information Management
- Access Rights
- User Authentication
- External Access
- Security Certification
- Computers and Shared Equipment
- Software
- Incident Reporting
- Education & Training
- Restricted Areas
- Security Audits
24 hour-control over the internet gateway to block and monitor external intrusion via internet network
In case of an intrusion from outside, CERT (Computer Emergency Response Team) is organized in accordance with the internal procedures of the Company to make a proper response. The CERT cooperates with an external analysis institution and relevant government agency and takes necessary action to minimize the damage.
In case of an intrusion from outside, CERT (Computer Emergency Response Team) is organized in accordance with the internal procedures of the Company to make a proper response. The CERT cooperates with an external analysis institution and relevant government agency and takes necessary action to minimize the damage.
By operating a firewall, we protect the important networks , such as DMZ and work/design networks and continue to monitor the traffic, simultaneously
The firewall allows only reliable traffic to communicate with the network and blocks unreliable traffic from network communication
Only authorized devices are given permission to connect to the wireless network
Network segmentation is a technology that operates the networks by separating them so that workers can perform their task in a completely separated environment. For semiconductor design work, which is the , which is the core competence of the Company. Nextchip separates the network for semiconductor design job from other general affair networks.
01.To transmit the data from separated network to general affairs’ network, workers need an approval by a separate procedure. Through this process, we can block the leakage of information related to design, fundamentally and completely.
02.In case of the members’ access to the network from outside through work from home situations, etc., we can provide a secured and safe VPM environment and support them to perform their job, effectively.
-
Entry control
Entry is permitted only to pre-authorized personnel. Entry control through biometric data and mobile verification process.
-
PC security
Virus vaccine installed in all PCs of the members to protect the information and prevent information leakage during their work performance, and to prevent data loss
Through DLP, only authorized PCs can access the internal network (Operating NAC”) and the access of the PCs with vulnerable security are restricted
*DLP: Data Loss Prevention* NAC: Network Access Control -
Introduction of DRM Solution
Application of encryption technology to all documents, and introduction of watermark operating DRM for internal printouts

